The Four Security Layers model
This topic describes the four security layers of Board and how they work.
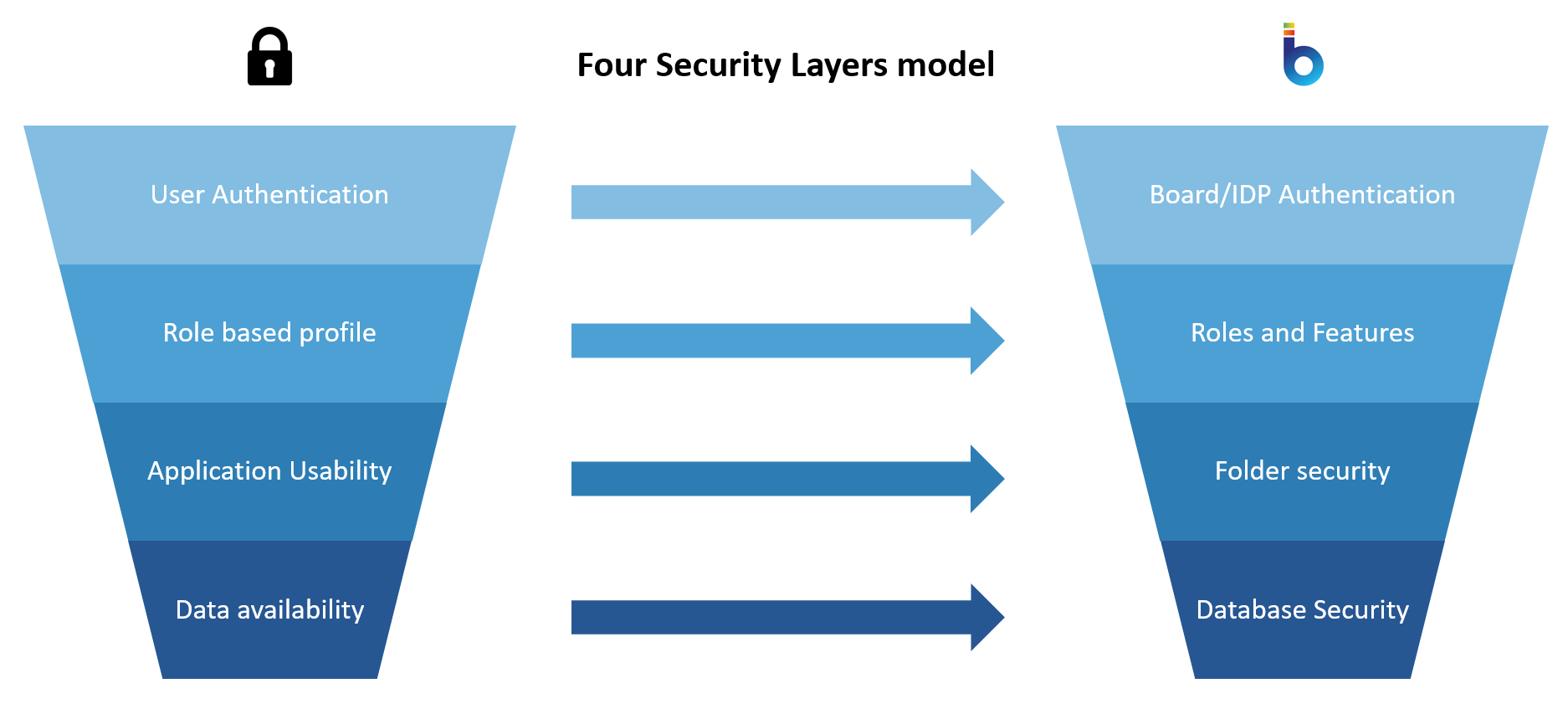
Board provides a robust yet very flexible security system. Access to the Board environment and Platforms can be customized from the highest level, which is basic user authentication, down to a very granular level, such as access to individual Cubes or Entities. This is achieved through four layers of security, which are the following:
- User Authentication (Board or IDP authentication methods which can be configured in the Subscription Hub)
- Role Based Profile (Roles and Application Profiles)
- Application Usability (Folder security profiles)
- Data Availability (Database security profiles)
First Layer - User Authentication
The first layer of Board's security system is user authentication. This is the process of verifying the identity of a user attempting to access your Board environment or its Platforms through a username and a password.
Users are managed at the Subscription Hub level. This means that users are not contained or managed in a specific Platform, but they are managed in the Subscription Hub where you can give them access to your Board environment and your desired Platforms with all needed authorizations and permissions.
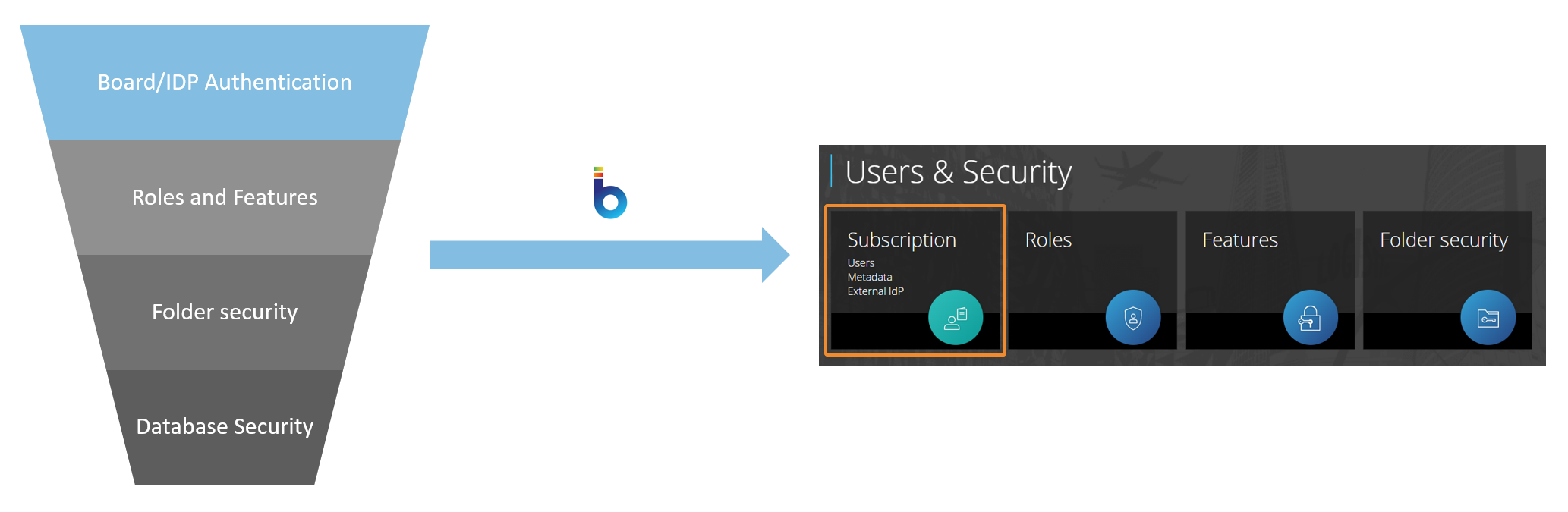
You can give users access to your Board environment through user authentication in several ways:
- By creating all necessary user accounts
- By importing a list of users from a file
- By using the Enrollment feature of the Subscription Hub
- Through an external identity provider (IDP).
When you create a user, you can decide the type of access that user has to your Board environment, which Platforms of your Board environment that user can access, and much more.
See the Users and Identity Provider Federation sections of the Subscription Hub for more information on how to create and manage users.
Second Layer - Roles and Application Profiles
The second layer of Board's security system comprises user Roles and Application Profiles, which define the user's access to data and elements of Data models and features of the Platform, respectively. Through Roles and Application Profiles, you can decide the following:
- Data model access. You can associate existing Database security profiles with the desired user Roles for each Data model: this way you can manage the type of access a user has to the Data models of a Platform
- Data model elements access. You can apply Security selections and Custom selection scripts on a user Role to give a user access to data only related to specific Entity members
- Feature access. You can configure Application Profiles where you can decide which Board features will be available to the user. For example, the ability to edit a Layout, edit a Procedure, perform selections, etc.
Roles and Application profiles are configured and applied at the Platform level. Each Board Platform has its own Roles, which in turn are asscoiated with Application profiles.
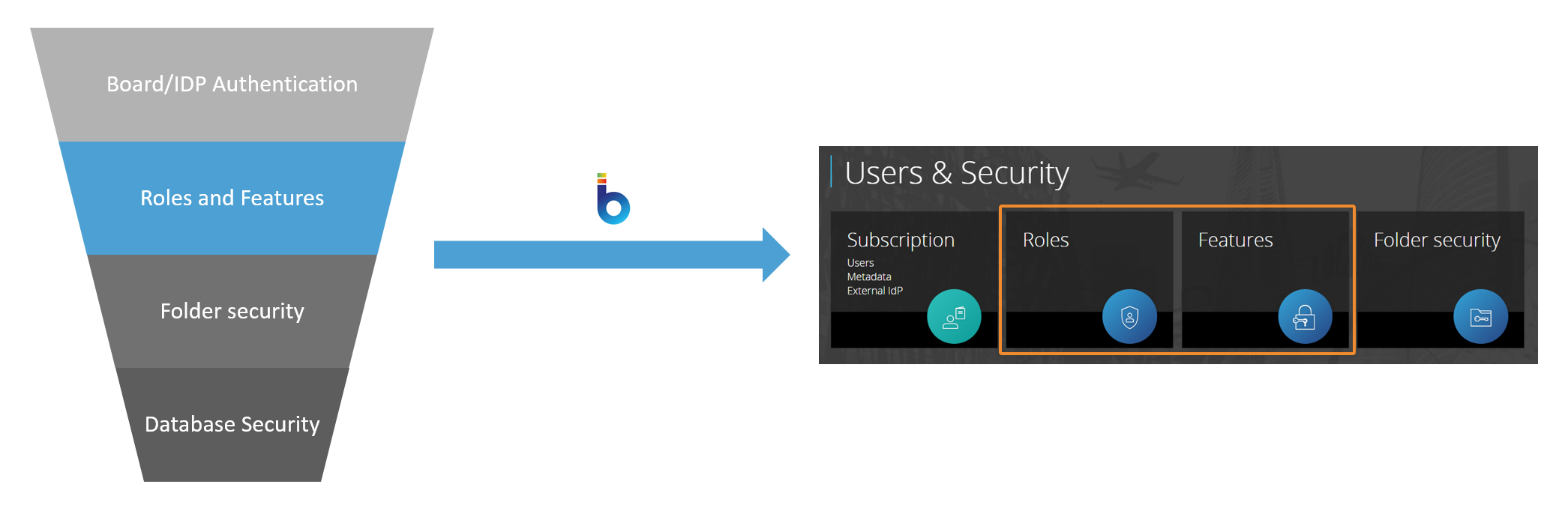
Roles and Application Profiles are very useful in cases when you have users who must have a different type of access to your Platforms, their Data models, and features.
For example, a Board developer that has to develop an application (a Capsule) must have full access to a Platform's Data models, data resources, and features, but a normal day-to-day user of that application may only need to access its Capsules to view data stored in Cubes and maybe perform Data Entry actions. In this case, a Role with full access is created and associated with the user accounts of the Board developers, while a Role with limited access is created and associated with the user accounts of all the day-to-day application users.
You can create and manage Roles in the Roles section, while Application Profiles can be managed in the Features section of the System Administration. Application Profiles are associated with Roles, and then Roles can be assigned to users from the User profile panel, through the Enrollment process, as with the Import users feature in the Subscription Hub.
Third Layer - Folder security
The third layer of Board's security system is Folder security profiles, which define a user's access to Capsule folders and single Capsules of a Platform.
Folder security profiles are configured and applied at the Platform level. Each Board Platform has its own Folder security profiles.
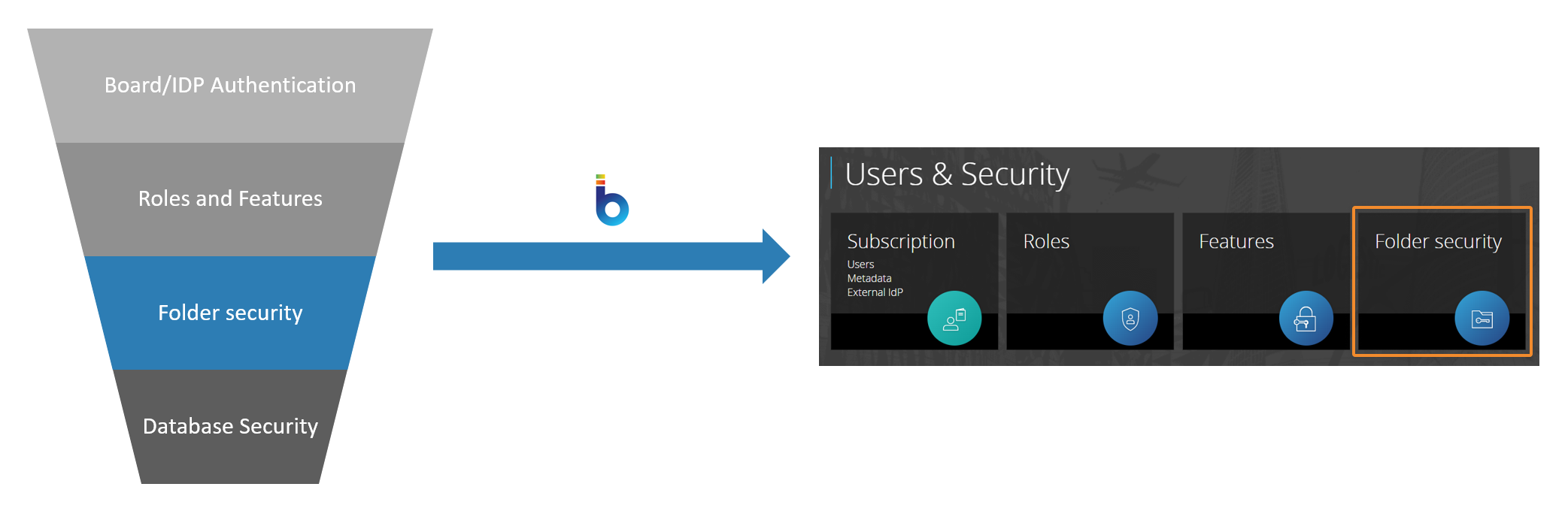
Users can access all Capsules and Capsule folders by default, however, there might be cases where users of the same Platform must have access to different specific Capsules. For example, the administrator of a Platform application made of various Capsules needs to access an "Administration" Capsule where he can configure different settings of the entire application, while normal day-to-day users of that application will not need to access that Capsule, since they must perform only functional tasks and not administrative tasks. In this scenario, you can organize Capsules in different Capsule folders and assign Folder security profiles to each user Role in order to establish different levels of access to the different Capsule folders.
You can create and manage Folder security profiles in the Folder security section of the System Administration area and you can associate them with Roles in the Roles section of the same area.
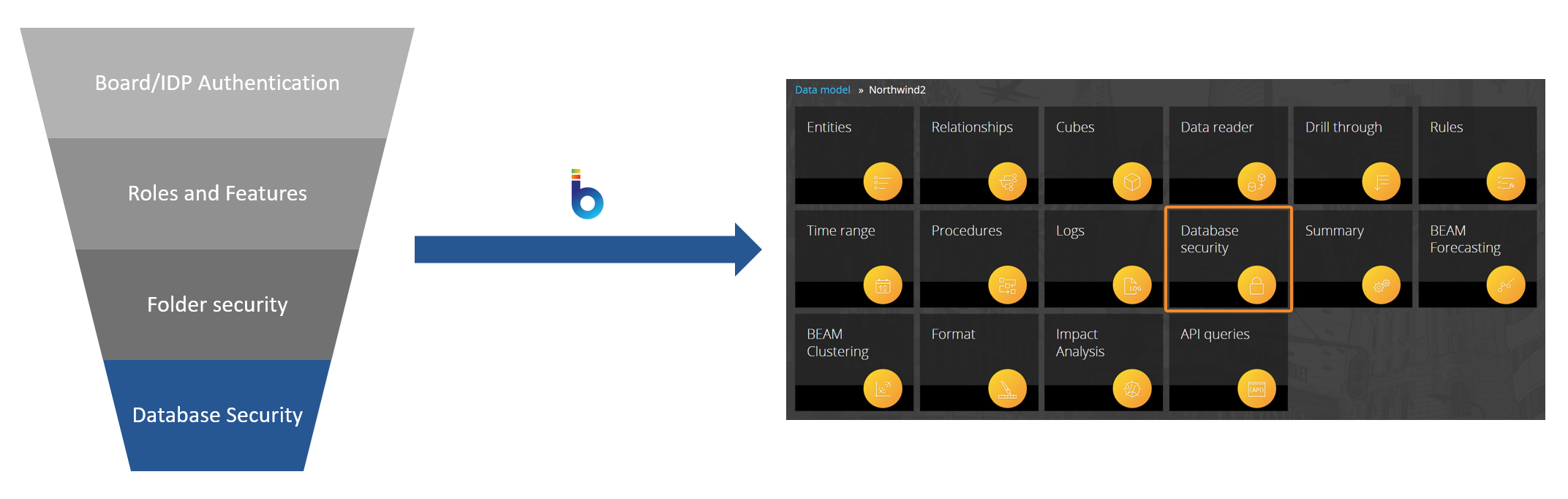
Fourth Layer - Database security profiles
The fourth layer of Board's security system is Database security profiles, which are a set of permissions and authorizations that define a user's type of access to a Data model, its elements and the data it contains.
Database security profiles are configured and applied at the Data model level. Each Data model has its own Database security profiles.
Database security profiles are essential to establish the type of access that different users of a company have to a Data model. For example, you may have the following three types of users with different types of access to the Data model:
- Administrator
- Planner
- Analyst.
Three Database security profiles are usually created as follows:
- ADMIN. This Database security profile is usually associated with users whose role is Data model administrator. These users usually have full access to the Data model design sections and all of its data and elements (Cubes, Entities, Data readers, etc.). They need to perform administrative and maintenance tasks on a Data model, therefore they must have full access to it
- PLANNER. This Database security profile is usually associated with users whose task might be financial planning. These users usually have restricted access to the Data model design sections and its data and elements. They may view data stored in Cubes and may perform Data entry actions on specified Cubes but cannot modify the Data model structure
- ANALYST. This Database security profile is usually associated with users whose task might be financial analysis. These users usually have restricted access to the Data model design sections and its data and elements. They can only view data stored in Cubes and cannot perform Data entry actions or change the Data model structure
You can create and manage Database security profiles in the Database security profiles section in the Data model design area, and you can associate them with Roles in the Roles section in the System Administration area.